There are various peer-to-peer protocols out there. All of them focus the decentralisation of storage and other system resources. Most implement a distributed hash table (DHT) to store information. That is, each node of the network only holds a small part of the hash table but is able to locate and retrieve any requested entry. Kademlia, a protocol designed by two NYU students in 2002, is one of them.
The Kademlia Protocol
Kademlia is based on four simple remote procedure calls (RPCs) and guarantees a very fast and lightweight exchange of information by using the connection-less UDP instead of TCP. Every node as well as every entry of the DHT is tagged with an identifier, called node ID or key. By XORing identifiers, one can calculate the distance between them and is hence able to walk through the network knowing whether one is near or far to a specific node. This so called XOR metric makes it possible to group the entries of the DHT around the K closest nodes to the entry’s key. An entry with the key 10, for instance, will be stored at the nodes with a node ID close to 10.
Kademlia + PKI = KadS: The Secure Extension
In my Bachelor thesis, I am going to extend Kademlia from a simple peer-to-peer protocol to a trusted and secure network. The proposed KadS network is almost identical to the Kademlia network, i.e. it consists of the described RPCs and implements the same XOR metric. The major extension to the protocol is that every node is equipped with a public/private key-pair signed by a trusted CA. This extends the normal Kademlia network to a public key infrastructure (PKI) in which every communication is encrypted, every node can be trusted and only verified nodes can participate in the network.
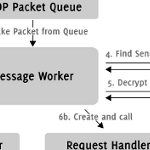
Every connection is synchronously encrypted with a session key which is created and exchanged in a handshake procedure when two nodes first meet. That is, a node has a different session key for the connection with each node it knows in the network. The handshake is similar to the one used in other software except for the fact that both clients exchange their public key and need to verify each others identity. After a successful handshake, two nodes are able to exchange lightweight encrypted messages using the session key and the basic protocol applies
An application: The distributed URL blacklisting service
As an application to the proposed KadS network, I chose a distributed URL blacklisting service. Please read more in my Bachelor thesis exposé, or simply download the whole thesis:
Blacklisting Malicious Web Sites using a Secure Version of the DHT Protocol Kademlia.

great project ! how is it going ?
All best,
Hey there,
Thanks for you interest.
After the Bachelor thesis, I haven’t had much time to further tweak and test the performance of the system, but the foundation works pretty well. As far as I know, the chair I wrote the thesis at is now using my code base to further develop it. I should probably ask them …
Regards,
Philipp
I felt you would be interested in this:
http://www.ijcsit.com/docs/Volume%204/vol4Issue3/ijcsit2013040333.pdf
It seems rather similar.