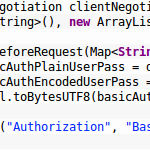
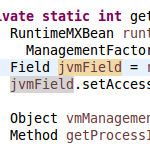
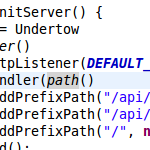
Snippet 0x08: HTTP Basic Auth for secure WebSocket connections (with Undertow)
For my open source file sync software Syncany, I use the embedded web server and web socket server Undertow to provide a websocket and REST based interface by the Syncany daemon. Syncany clients (such as the GUI, or potentially a web interface) connect to this daemon, send requests and receive asynchronous events. Syncany’s GUI client also uses the Undertow websocket client to connect to the above mentioned daemon.
To authenticate the websocket client with the daemon, the simple HTTP basic authentication mechanism over HTTPS is used. This tiny post shows you how to authenticate against a websocket server with HTTP basic auth using the Undertow websocket client.




Recent Comments