
Adobe’s proprietary Flash format has become a significant part of the Internet as it is today. While its importance in Web applications is slowly decreasing due to Web 2.0 technologies and HTML5, it is still a major player in the browser game and application sector. The majority of these games and applications are for entertainment only and offer you nothing but a nice rank in the high score. On rare occasions, however, there are Flash games in which you can actually win something valuable such as concert tickets or even money. And of course there are applications that let you stream, but not download content from a website.
So what’s the problem with that, you think? The problem is that almost all Flash applications can be hacked very easily and most developers are not aware of that.
As a reminder of how vulnerable Flash applications are, this post aims to raise awareness for these issues. In a case study, it shows how a Flash-based game and its server side high score can be tricked within a few minutes using free tools only.
Contents
Disclaimer
This post is meant to raise awareness for the vulnerabilities of Flash-based applications. It is not a hacking tutorial or how-to. For that reason, I will not describe all steps in great detail, but only sketch the basic steps.
1. Introduction
1.1. The problem with Flash applications
Flash applications are similar to normal Windows/Linux executables: Like normal programs, their source code is compiled to a binary format and later executed on the client machine. The major difference to .exe or Linux binaries is that decompiling is a lot easier: while a C or C++ compiler translates the source code into machine code, i.e. CPU instructions, SWF files contain the ActionScript code in plain text. That is with the right tools, extracting the complete code is a no-brainer!
Combining this with the fact that sniffing into the client-server communication is also not the most difficult task, one can easily simulate the Flash client with own code snippets and scripts, and thereby send forged requests to the server.
1.2. Checksums as a solution?
Most application developers at least know that the client-server communication can be sniffed into. As an attempt to make it more difficult for people to send forged requests to the server, applications mostly use a message authentication code (MAC) or some other checksum-based mechanism. So instead of sending a plain text update query to the server (1), the application creates a hash by concatenating the user input with (to the user unknown) other data (2):
| (1) Without checksum mechanism | (2) With checksum mechanism |
|
POST /write-highscore.php HTTP/1.1 Host: www.example.com User-Agent: Mozilla/5.0 … … name=Phil&score=40 |
POST /write-highscore.php HTTP/1.1 Host: www.example.com User-Agent: Mozilla/5.0 … … name=Phil&score=40&check=283647a… |
This mechanism is completely based on the fact that the user does not know how the checksum is created. While this approach is very effective in regular applications, it completely fails in Flash programs: disassembling a Windows or Linux binary is very difficult and requires know how in assembler. Decompiling SWF files, however, is fairly easy and can be done in under a minute. That is retrieving the code that generates the checksum is only a matter of seconds.
1.3. Tools and basic approach
The following steps present a generic approach on how any Flash application can be exploited like described above.
Required Tools:
- Firebug (was at: https://addons.mozilla.org/en-us/firefox/addon/firebug/, site now defunct, July 2019, use F12 tools instead): Firefox plugin for basic communication sniffing
- Sothink Flash Decompiler: required to extract ActionScript code (trial version is sufficient)
- Wireshark: required for detailed communication sniffing (byte-for-byte)
Generic Approach:
- Enable Firebug and start sniffing with Wireshark.
- Go to the target web site and play the game or use the application.
- Look at the communication of the Flash application with the server. If there are any parts of the requests that cannot be recreated without the source code, e.g. checksums, download the important SWF files and decompile them.
- Analyze the ActionScript code and find the part which creates the checksum.
- Make a script that generates the same request with arbitrary input data, e.g. any score or name. For this script, the checksum algorithm from the ActionScript code can be used (or recreated).
2. Case study: a car parking game (with high score)
Our local newspaper Mannheimer Morgen recently hosted a competition in which users had to park a (virtual) car into different parking spots without damaging the car and with minimal fuel usage. Prizes were a safety training and concert tickets. While in this case the score of the participants did not decide who won (winners were drawn by lot), the winner in other competitions might be the one with the best score. Please note that I did not take part in this competition and I did under no circumstances try to win the prizes.

Parking Game: The target application in this case is a game called “Parking”.
2.1. Capture the client-server communication
Following the instructions from above, the first step is to capture the communication between the Flash client and the server. In this case, we are particularly interested in how to add our name with an arbitrary score to the high score list.
Firebug:
Using Firebug, we can see three interesting requests:
- savescore.swf is the part of the client that is responsible for sending the score to the server.
- serverdate-read.php is called by savescore.swf for no obvious reason – very suspicious. We will later see that the result is used in the checksum generation.
- highscore-write.php is also called by savescore.swf and actually writes the user’s score to the database on the server.
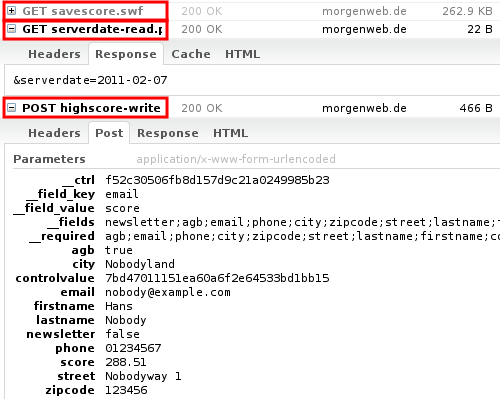
Firebug identifies the interesting files and requests.
In this case, three requests are relevant for the high score forgery.
What is particularly important is the two parameters __ctrl and controlvalue. Both are obviously generated by some checksum function in the savescore.swf-file. So the next step is to decompile the SWF file and look for the checksum-generating function.
Wireshark:
If we additionally enable Wireshark, we can get a plain text (or hex) representation of the HTTP request-response cycle. That is particularly important if one wants to forge a request in a way that it cannot be detected by the server.
2.2. Decompile the SWF file and find the checksum algorithm
Using the SWF Decompiler software (trial version is sufficient), the savescore.swf can be examined very closely. Most of the applications are not very complex and the relevant code pieces are found very easily.
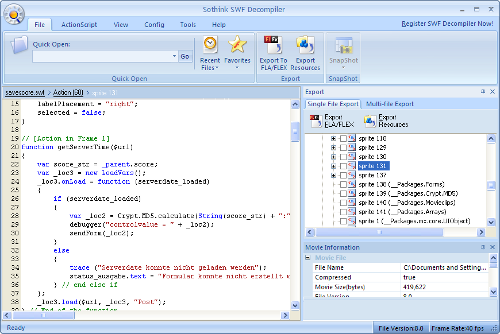
When analyzing savescore.swf, the two parts in which the checksums are created are found at different positions in the file. The __ctrl parameter is generated by taking a MD5 hash over the two concatenated values of score and email. The controlvalue parameter is created in a similar fashion and involves the previously queried serverdate.
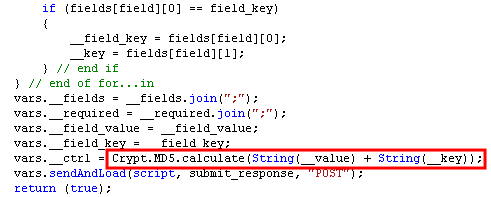
The __ctrl parameter is a hash value over two of the variable input parameters.
The controlvalue parameter is created similarly.
2.3. Write a script
Once it is clear how the checksums are generated, the puzzle is solved. The only thing left is to write a script that allows entering arbitrary input values, and using the previously determined checksum-mechanisms to generate a MAC.
Here is a short excerpt of how this could look like (using PHP):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
$score = "999.999"; $email = "nobody@example.com"; $data = array( "__ctrl" => md5($score.$email), ... "score" => $score, "controlvalue" => md5(...), ... ); foreach($data as $k=>$v) $data_enc[] = urlencode($k)."=".urlencode($v); $req = "POST /parking/highscore-write.php HTTP/1.1rn" . "Host: www.morgenweb.dern" ... . join("&",$data_enc); $fp = fsockopen("www.morgenweb.de", 80); fwrite($fp, $req); while ($line = fgets($fp)) { } fclose($fp); |
3. Conclusion
This blog post introduced a common way to outsmart Flash applications and games. It demonstrated that by sniffing into client-server communication and decompiling SWF files, many Flash applications can be misused. Using the example of a Flash game, the post showed that SWF cannot be compared to Windows/Linux binaries, but must rather be seen as JavaScript-like client code.
Even though this post only demonstrated this using a rather harmless game, more serious misuse is also possible. Flash-based music streaming sites such as Simfy (was at: simfy.com, site now defunct, July 2019), Spotify or Grooveshark (was at: grooveshark.com, site now defunct, July 2019) are affected as well. They all use a similar mechanism for their Flash-based music player. Using the approach presented above combined with tools like rtmpdump can potentially harm their services significantly.
Flash once was a great way for bringing a little dynamic in the Web 1.0, but is now outdated. With various JavaScript frameworks and HTML5 on the way, Flash is going to retire soon. Developers and companies must be aware of the flaws of Flash and adjust their services accordingly to make sure that they cannot be misused.

thanks for the detailed post. I never knew about flas game hacks in details. Appreciate your time.
Nice post i must say. I run an online betting platform which happen to use a flash player for a virtual football game. Are this attacks applicable? In winning bets
Hi Bob, In theory, they are of course applicable — unless you have built in server-side mechanisms to prevent them… I’m not an expert though — just a wanna-be-hacker :-)
Hi philip,
i am trying to hack a flash game (maze) before i was able to edit the headers and change the score before re-sending, but now whenever i change the score above a 1600 when i resend the page redirects to google.com and the score doesnt change. while before i could change it to any number i want. any help on this?
Sorry can’t help you with that with the information you gave me. Did you monitor the request/response cycles with Wireshark? Post some screenshots…
Hi Philip,
I am an avid online game contestant and I must say I am quite good in it too. But because of the lack of hacking knowledge, I am losing out to those who know.
The game organizer usually ignore our pleas and when we try to tell them of such misuse, they just brush them aside.
Is it possible that you help us out if we can give you the links to such game and you try and replicate what they are doing to get such high scores?
I am tired and fed-up with people cheating and grabbing all the prizes right under our nose.
hey man how to hack tanki online
hi heckel, pls how can i use wireshark for sniffing, i tried applying ur details given to me but it wouldnt work, any help…pls
Simply open Wireshark as root/Administrator, and then use the Capture function to start sniffing. There’s lots of good Wireshark tutorials out there.
hi philipp can u make cheat tools for pockie pirates game?? i dont have any knowledge for hacking .. please
Hi.
Are this guide useless on thn facebook game “Criminal Case”?????
hi pilipp, :)) can you guide me how to hack waroftitans?? can we use swf files to change value???
Hi i wanna say thank you,but i do have 1 more question. Is it possible to add credit to an account on a fairly popular server sided flash game with only 1 program , tool ? or all are those? just scams?
i always find trojans hiding in those tools…
You wrote : “Flash once was a great way for bringing a little dynamic in the Web 1.0, but is now outdated. With various JavaScript frameworks and HTML5 on the way, Flash is going to retire soon.” …Flash is for vector graphics !!! That made very light animations and games…
That is FLASH ! Don’t compare html 5 and flash please. flash is certainly not over. this is the propaganda of the concurents launch on the web…don’t compare apples and pears.
Hello youda,
Perhaps my introduction isn’t exactly fair to compare the not-yet-comparable capabilities of HTML5, JS and SVG vector graphics with the overall capabilities that flash delivers. However, I strongly believe that the end of the flash era is near. And given that flash can be decompiled, developers should not assume that their code is safe from hackers and wanna-bes (like me)…
Hope you still liked the article
Best regards,
Philipp
Thats great, we can also traget games like Crazy Taxi on Facebook and more flash based game websites. To make it more easier cheat engine can be deployed too.If you finding the above method quite geeki.
Very interesting study, and as a long time gamer, have to say, I’m not surprised.
I’m curious though, what do you think about Unity 3D? As a potential replacement for flash in web-browser games I mean.
Im trying to see whats going on on this page but im not sure what am i doing wrong. Is it even possible to hack it? http://wod.browsergame.com/event/dig/
thank you very much sir :) nice to meet you, please email me :)
hey can you please help me ? how to cheat kabam godfather ??
hack octro teen patti flash games plz reply
@vivek: I’m not hacking anything for anyone. :-)
Hey,If a game does show anything in networks than how can we maniplute that game i mean how can we hack it.As there is no client server communication so how do we make change in front end manually.There is one game path to success for that can you tell me please.
Hi, i’d like to know if is possible to hack a game with this “guide”, the game is Hobbit armies of third age. Hope in your answer.Thx for your time.
Are games such as WGT Golf hackable in this manner? It’s purely online and to my knowledge everything runs within ‘its’ environment. I’m just trying to ascertain if the people who are posting crazy low scores are in fact manipulating the game within their browser.
There is a program that delays mouse interaction which allows fairly accurate mouse click prediction, it’s not perfect, but does to what it says for the most part. Doesn’t really help much from my understanding.
I don’t know this game in detail, but in principle (and to the best of my knowledge), at least all user inputs in flash games can be manipulated in this manner. Sometimes it’s easier, sometimes it’s a bit more difficult. But it should always be possible.
Obviously developers can prevent those kind of manipulations by double-checking if values, request counts/times and such things are “sane”. For example, if a request is repeated n times in the exact manner, or if the number of requests exceeds x requests/minute, you could ban a user.
is it possible for the owner of the flash game to find out if your hacking or not and if so how easy is it???
Hi Joshua, that obviously depends on the game, but the only real chance you have is to check request logs in your web/application server and match them to what requests you’d expect. So for example, if your application always requests /checkscore.jsp before /sendscore.jsp, you could check if that happens with all the /sendscore.jsp requests.
Another way would be to limit the amount of retries for a certain request in a specific amount of time, or to log IPs that try too often. Those are obviously just indicators, but they can be implemented without changing the flash game itself. You can implement those things on the server side.
Can facebook game miscrit be hacked in similar way?
Hey, i have a online slot gaming site, does that method works on my site as well? if so what can i do to prevent it.
hello mr C. Heckel
can you help me to hack this game? —> http://io.gamgos.net/
I actually design and develop tools to guard against this and other ‘stuff’ the gamers try to pull in existing games and judging from the reactions here I’d better go to yellow alert : all the ‘kids’ will be out trying their new-found wisdom. Still, gratifying to see someone describe some the issues — just a fraction — we deal with, with knowledge rather than ‘glitch’-voodoo and game myths.
Thanks for the nice words. You can’t believe how many e-mails I get from people asking me to “hack” stuff for them — even though I consider myself a script kiddy :)
I also use this software to do but just decompile the game simple. As complex game we will have difficulty
good step , i want know how you send file swf to server .
ty before
Seen better tools in the past recording ip packets and playback unfortunately it can’t be found again it could be used for all flash games and java games.
Hi Philipp … Just have a question on my mind that where do i find any facebook game server file for example SWF fille.. !
i need help hacking this online game its very popular its called avakin life. You play the game by downloading the app but all data is stored on the backend
i need help hacking this online avatar game its available in the andriod store, but all the data is stored on a backend
Hi Philip
It’s a great article well , i don’t understand how a php will interact with server or where we have to use this script? can you please explain that part and is checksum same as hash function and does server calculates again checksum from the string and compares with the checksum sent from client to know whether packets are editted or not? Would you please like to explain
Thanks
hello, i have a online slot gaming site , and i wonder if that method works on on my site? i don’t want to somebody hacked this games. if you can please answer me and if so what should i do to prevent it
Hey Philipp, thanks for this tutorial. While it is from 2012, I still find this useful for hacking flash games. One quick question, lets say I hacked an online flash game and gave myself 10million coins, would the coins only be visible on my side or can I actually spend them in the store?
hey phillip!
I really suck at this game and i want to hack it, so please waste some of your time and make me a easy tool so I can download and install it and be the very best like no one ever was in and I can’t do it myself because I can’t hack, and I dont want even to learn the basics of programming because I’m wasting my time on these shitty games in the first place.
And for all that time wasted, I’ll give you my thanks and no payment whatsoever, because theres like 6 billion programmers out there and if you can’t do it i’ll ask some indian codemonkey.
Thanks
The average poster